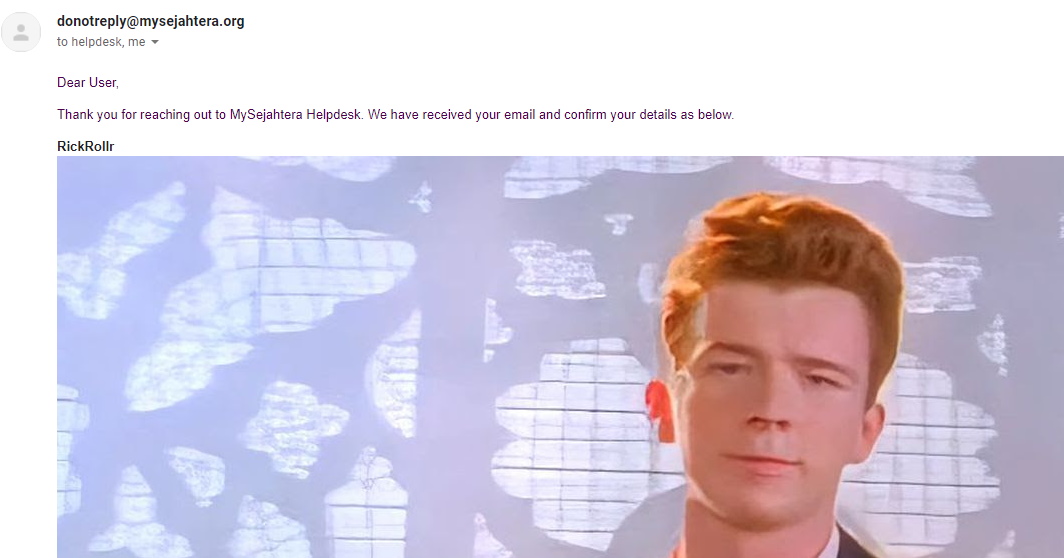
Instead, MoH insists that they were triggered through API manipulation. Specifically, the API is related to the MySejahtera Check-In feature that allows the public to generate MySejahtera’s QR code for them to display at their premises. Random phone numbers and e-mail addresses were used as the target recipients for the unsolicited OTP SMS and e-mail. In addition to that, MoH noted that the unknown party has also taken advantage of the Need Help feature within MySejahtera’s website to send random spam e-mails. The agency further added that the level of security for both MySejahtera’s app and website has since been increased. However, the media statement didn’t provide any details on what exactly that the MySejahtera team has done in order to accomplish that. While the statement did not make any direct reference to them, the API manipulation seemed to be related to the vulnerabilities that were discovered recently by full stack engineer Phakorn Kiong. Given what has transpired for the past few days, MoH and National Security Council may want to consider conducting a thorough audit on MySejahtera to ensure that the platform is secure and reliable enough to continue serving the Rakyat as the national COVID-19 app. (Source: KKM / Twitter.)